Overriding ISP DNS server settings in pfSense

I'm not really a fan of using my ISP provided upstream DNS server; besides the lackluster performance, there's also some serious privacy concerns.
When you visit a website — or, in other words, make a DNS query — your ISP can collect your IP address, target hostname, and target server IPs. This is known as a DNS leak.
My edge router happens to be a spare desktop machine that I've repurposed into a bare metal pfSense+ device - I slapped in a Intel X540-T2 dual 10Gbps port network interface card (I'm currently on Bell's 1.5 Gbps Fibe internet on a Sagemcom GigaHub modem - but I figured if I ever wanted 3+Gbps, this would be somewhat futureproof)
Under System > General Setup, specify 1.1.1.1 (Cloudfare) - you could also reliably use 8.8.8.8 (Google). I'm using Cloudfare already so I've gone with that. I'll create a subsequent blog post comparing the performance of some of the well-known public DNS servers.
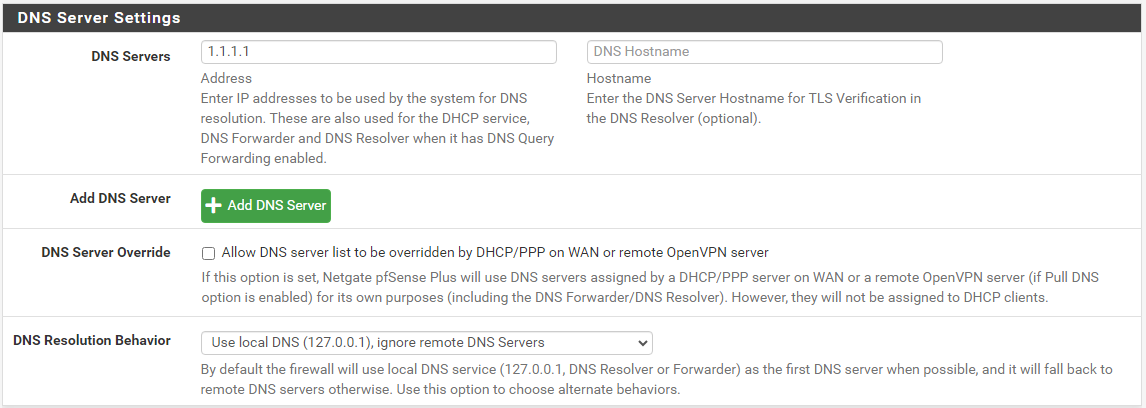
Uncheck the box that says Allow DNS server list to be overridden by DHCP/PPP on WAN.... Note how I've also set the DNS resolution behavior to ignore any remote DNS servers.
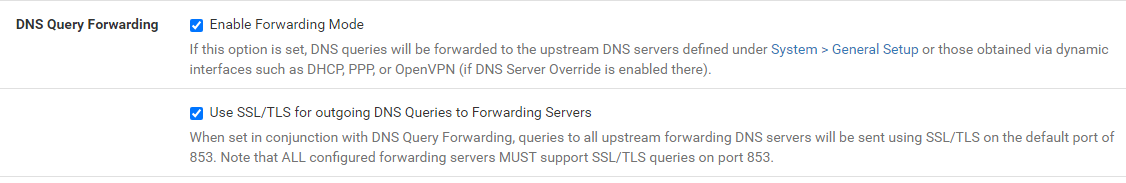
Under Services > DNS Resolver > General Settings,
- Check
Enable DNS resolverif not already. - Check
Enable Forwarding Mode- If this option is set, DNS queries will be forwarded to the upstream DNS servers defined underSystem > General Setupwhich we had set to be Cloudfare's 1.1.1.1
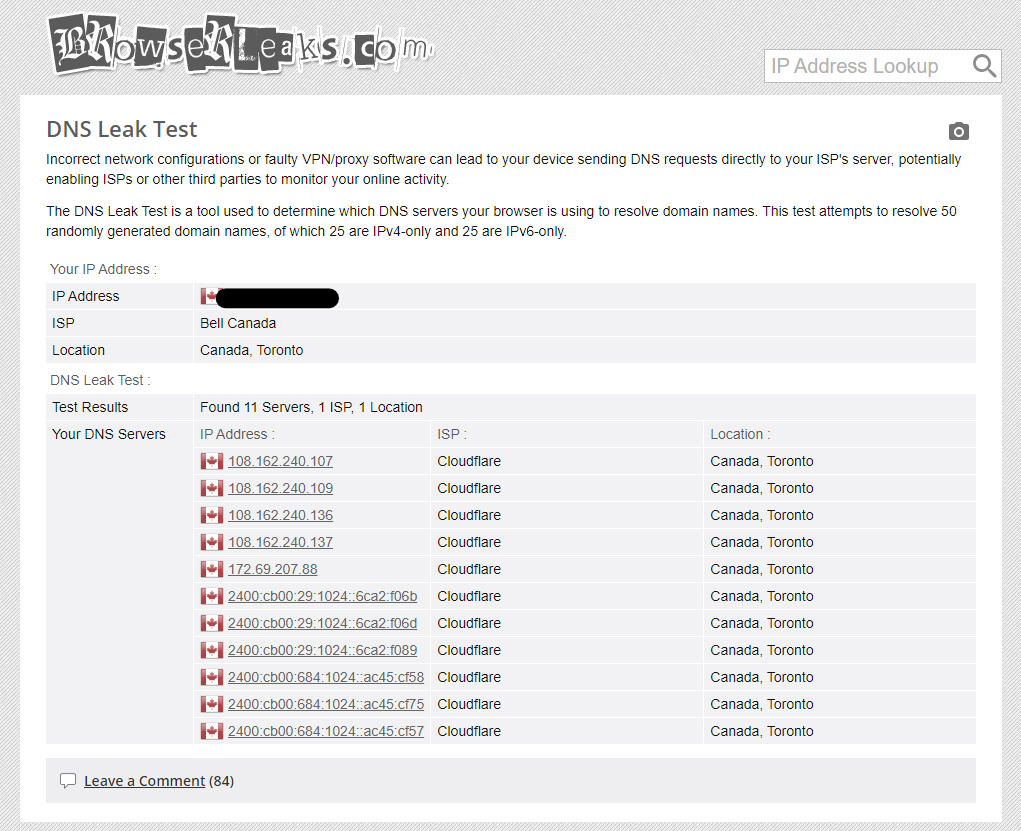
To verify your settings, try a site that does a DNS leak test such as https://browserleaks.com/dns